|
<< Click to Display Table of Contents >> Security |
  
|
|
<< Click to Display Table of Contents >> Security |
  
|
Cimera implements a very granular security model and can be applied to Buckets, Item Types or even extending down to the individual Attributes of an item.
Additionally security can also be applied depending on the Lifecycle state of an item, or Promotions of an item can be restricted to only authorised users.
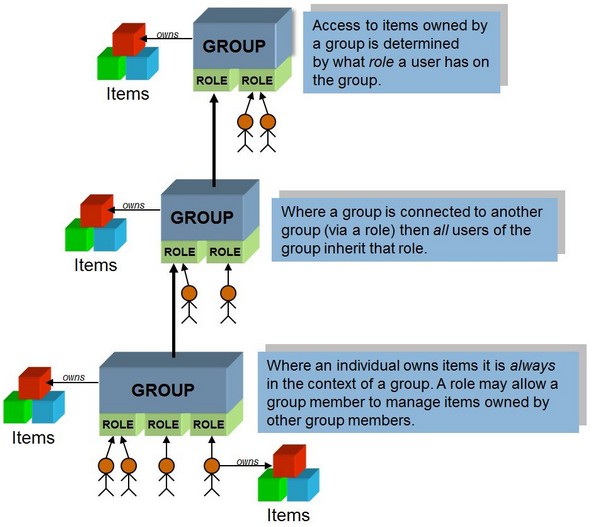
Every item in Cimera must be owned by either a Group or a member of a Group. This encourages accountability and enables effective security. Additionally if Workflow is required then an item can be assigned to a Group or member of a Group.
Access is role-based and each user may be given multiple roles on multiple groups.
Combinations of
| • | Groups |
| • | Roles |
| • | Users |
| • | the owner |
| • | the current Assignee |
are then given access to items or types of items.
Removing Read Access
By default all users have read-only permissions on all items. Hiding items and removing read access is applied at either Bucket level or Item Type level
See Security in the Cimera Administration Guide for details
See Also
Further details of Cimera Security are found in the Cimera Administration Guide